

The advantage of having functions such as 'Create Object', 'Read Object', 'Update Object' and 'Delete Object' in separate tasks or transactions is that it becomes a very simple matter to grant or deny access to individual functions simply by setting or unsetting a switch on the Menu database. This means that all security checking can be performed in the menu system before a transaction is activated rather than within the transaction itself after it has been activated.
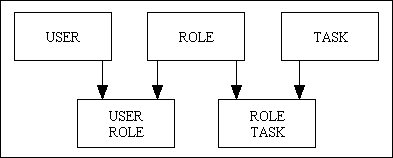
The list of Tasks which a User is allowed to access is known a Security Profile, Access Profile or Access Control List, and is held on several tables in the MENU database, as shown in Figure 1.
Each User must belong to one or more of these Roles, so by changing the Access Profile for a Role you effectively change the Access Profile for all Users of that Role. Each USER-ROLE has a sort sequence and a start and end date. The dates allow a particular entry to be valid for a particular range of dates. When the entries are read for the current date the one with the lowest sort sequence will provide the user's start task, global access and external authentication.
Figure 1 - Database structure
There are two ways of viewing and maintaining the contents of the ROLE-TASK table:
The contents of the USER-ROLE table can be viewed using the List User Role screen.
This Access Profile is used in two places:-
